Changing SELinux Modes
Traducciones al EspañolEstamos traduciendo nuestros guías y tutoriales al Español. Es posible que usted esté viendo una traducción generada automáticamente. Estamos trabajando con traductores profesionales para verificar las traducciones de nuestro sitio web. Este proyecto es un trabajo en curso.
Security Enhanced Linux is a Linux security module for mandatory or role-based access control. SELinux is packaged with CentOS and Fedora by default, and can be running in one of three modes: disabled, permissive or enforcing.
Ideally, you want to keep SELinux in enforcing mode, but there may be times when you need to set it to permissive mode, or disable it altogether. Note that the disabled state means the daemon is still running and is still enforcing rules for discretionary access control, however no MAC security policies are being used, and no violations are being logged.
NoteTo use SELinux on CentOS or Fedora, you must use the distribution-supplied upstream kernel (as opposed to the Linode-supplied kernel, which does not support SELinux). All recently created Linodes run an upstream kernel by default. Review the How to Change your Linode’s Kernel guide for more information on upstream kernels, the Linode kernel, and how to switch between them.
View the current enforcement mode of SELinux on your system using
sestatus. You can see below that SELinux is set to permissive mode.[root@centos ~]# sestatus SELinux status: enabled SELinuxfs mount: /sys/fs/selinux SELinux root directory: /etc/selinux Loaded policy name: targeted Current mode: permissive Mode from config file: permissive Policy MLS status: enabled Policy deny_unknown status: allowed Max kernel policy version: 28Change to enforcing mode using
setenforce. This will be for the current runtime session only. You’ll need to edit the SELinux configuration file if you want the setting to survive a reboot.setenforce 0 # Set to permissive mode. setenforce 1 # Set to enforcing mode.Edit the SELinux configuration file so your mode change will survive reboots. The
sedcommand below is given as an example, and will switch from permissive to enforcing mode. For a different mode configuration, just substitute the two words in the command with the mode you currently have, and the one you want to enable (ex. disabled to permissive).sed -i 's/SELINUX=permissive/SELINUX=enforcing/g' /etc/selinux/configIf you prefer to edit the file manually, it should look like this:
- File: /etc/selinux/config
1 2 3 4 5 6 7 8 9 10 11# This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - No SELinux policy is loaded. SELINUX=enforcing # SELINUXTYPE= can take one of three two values: # targeted - Targeted processes are protected, # minimum - Modification of targeted policy. Only selected processes are protected. # mls - Multi Level Security protection. SELINUXTYPE=targeted
Reboot your Linode. During the bootup process, SELinux may need to run a relabeling of the filesystem. It will handle this automatically and when it’s done, it’ll reboot the system. If you do not have Lassie enabled, the Linode will shut down and you will need to manually reboot in the Linode Manager.
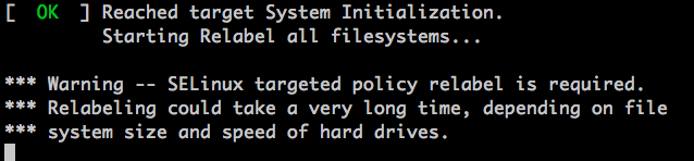
When your Linode boots back up, log in and verify that SELinux is now running in the new enforcement mode. Run
sestatusagain. The output should show that you’re in the mode you set in steps 2 and 3 above.[root@centos ~]# sestatus SELinux status: enabled SELinuxfs mount: /sys/fs/selinux SELinux root directory: /etc/selinux Loaded policy name: targeted Current mode: enforcing Mode from config file: enforcing Policy MLS status: enabled Policy deny_unknown status: allowed Max kernel policy version: 28
More Information
You may wish to consult the following resources for additional information on this topic. While these are provided in the hope that they will be useful, please note that we cannot vouch for the accuracy or timeliness of externally hosted materials.
This page was originally published on





